Top 10 Tools of Ethical Hacking
Being an ethical hacker is not only a profession – it is an exciting quest in the space of the internet. Ethical hackers are the advocates of the digital space and for them to defeat evil hackers, they require the best weaponry. But let’s be real: tools of ethical hacking are much more than programs – they are the applications that represent modern Excalibur in the fight against cyber threats.
Whether you are a beginner who is keen to learn, a future certified ethical hacker, or a professional in the field of cybersecurity, this guide to the tools of ethical hacking will lead you through the technology that protects the new digital frontier.

Why Tools of Ethical Hacking Are Game-Changers
For instance, visualize a locksmith who has been hired to create a lock for a vault. The job is almost undoable if the right tools are not found in the process. In the same way, the tools of ethical hacking are to be used for similar purposes in the cyber world. They expose weaknesses, enhance security, and even give one understanding of how a network or an application stands in relation to an attack.
These tools of ethical hacking allow hackers to:
- Identify weak spots and open ports on the networks.
- Use live attacks to check the effectiveness of existing or intended prevention strategies.
- Threat analysis to come up with prevention and control measures.
- Reset passwords so that the strength of authentication can be tested.
Without further ado, here are the top 10 tools of ethical hacking that are defining the industry. Each of the tools is a work of art on its own not only simply because they are developed for a particular purpose but because they perfectly combine to create an ideal ethical hacker’s kit.
1. Nmap: The Network Detective
Nmap is one of the ethical hacking scanning tools that act as a magnifying glass against vulnerabilities like open ports. In essence, it is a network exploration and security auditing tool used by computer system administrators and ethical hackers to gather information on a given network. It runs from host identification to service and operating system identification and is valuable for pre-attack planning or commonplace network scans.
Be it scanning a single IP or large sub-net Nmap is very effective in providing specific and timely results. Its versatility can connect to other forms of more extensive penetration testing processes making it vital in the cybersecurity space.
What Makes Nmap Legendary?
- Host Discovery: Instantaneous discovery of active network hosts. Ethical hackers use this to find out how far they can go while testing an organization’s system.
- Port Scanning: Nmap shows which ports are open, shut, or filtered and which ports are potentially vulnerable to exploitation.
- Service Version Detection: Identify the applications that are running on open ports, and their versions, to detect outdated or vulnerable software.
- Operating System Detection: Identify the OS type and version on target systems to make the right assessment during the penetration testing tasks.
- Scripting Engine (NSE): Uses a strong script to automate activities such as vulnerability scanning and carrying out network audits.
- IPv6 Support: The new generation scanning with the possibility of working in IPv6 and wide coverage.
- Customizability: Nmap has a very wide variety of commands and options available, many of which can be tailored to fit a particular scan.
Why Ethical Hackers Swear by It:
- Open-Source and Free: Nmap is free to use it is widely used and people can add to its functions and options frequently.
- Cross-Platform Compatibility: In terms of compatibility, Nmap is a network mapping tool that is compatible with Windows, Linux, and even macOS.
- Stealth and Precision: Ethical hackers actually have decisions to make; they can use the -sS which is the stealth scan or the -T4 which makes operation more swift and aggressive.
- Integration-Friendly: To mimic a real-life environment you should involve Nmap tools in conjunction with other tools such as Metasploit.
Pro Tip: You can use Nmap with Zenmap (an interactive graphical interface created for Nmap) for better management.
Popular Nmap Commands Every Ethical Hacker Should Know
1. Basic Scan:
nmap [target IP/hostname]Discover basic information about a host.
2. Scan Multiple Hosts/Subnets:
nmap 192.168.1.0/24Scan an entire subnet for active hosts.
3. Service and Version Detection:
nmap -sV [target IP]Identify software versions running on open ports.
4. Operating System Detection:
nmap -O [target IP]Determine the operating system of a host.
5. Custom Port Range Scanning:
nmap -p 1-1000 [target IP]Scan a specific range of ports for activity.
6. Using the Nmap Scripting Engine:
nmap --script [script name] [target IP]Perform tasks like vulnerability scanning using NSE scripts.
2. Metasploit: The Ethical Hacker’s Arsenal
When it comes to hacking, Metasploit can be regarded as being among the best certified ethical hacker tools. It is an open-source tool, utilized in penetration to test and assess security risks that a particular system poses to the attacker. Metasploit was created by HD Moore in 2003 and is a toolbox used to facilitate specific tasks of white hat hackers.
Metasploit is great for beginners in cybersecurity or anyone who is starting their journey with cybersecurity from scratch up, this tool is almost as versatile as possible.
What Sets Metasploit Apart?
- Exploit Modules: Several aspects of covert operations in Metasploit are designed to penetrate and take advantage of weaknesses in software or hardware.
- Payloads: These are scripts or tools deployed to a targeted system after gaining control over it. Popular payloads include:
- Meterpreter: A comprehensively loaded, memory resident payload that allows real-time manipulation of the infected system.
- Reverse Shells: It permits the attacker to get remote access to the target machine.
- Auxiliary Modules: Application for port scanning and service enumeration and for making DoS and DDoS attacks without using exploits.
- Post-Exploitation Tools: Collect information, escalate privilege, or maintain access on the compromised host for further use, analysis and.
- Encoders: These obfuscate payloads to avoid being detected by antivirus and intrusion detection systems (IDS).
- Metasploit Pro: It involves a paid version with more sophisticated features such as that of organizing phishing attacks and assessing web applications.
Getting Started with Metasploit
- Installation:
Metasploit runs on multiple platforms, including Linux, Windows, and macOS. It’s commonly used with Kali Linux, a penetration-testing-focused operating system.
Install via terminal on Linux:
sudo apt install metasploit-framework
- Launching Metasploit:
Start the framework by typing:
msfconsole
- Basic Commands:
- Search Exploits:
search exploit_name - Select Module:
use module_path - Set Target Information:
- set RHOST target_ip
- set LHOST attacker_ip
- Launch Attack:
exploit
- Leveraging Meterpreter:
Post-exploitation, use Meterpreter to interact with the compromised system:- meterpreter > sysinfo
- meterpreter > getuid
- meterpreter > download [file_path]
Popular Metasploit Modules
- Exploit Modules:
- ms08_067_netapi: Exploits a Windows Server vulnerability.
- android/meterpreter/reverse_tcp: Targets Android devices.
- Auxiliary Modules:
- scanner/portscan/tcp: Conducts a TCP port scan.
- scanner/http/http_version: Detects HTTP server details.
- Payload Modules:
- windows/meterpreter/reverse_tcp: Provides a Meterpreter session.
- linux/x86/shell_reverse_tcp: A reverse shell for Linux systems.
The Secret Sauce:
Metasploit is a training ground where one can hone the creation of the best ethical hacking tools with Python while tweaking the assemblies to the specific requirements. Metasploit is the framework for every emulation; it can be used for simulating a phishing attack or testing a firewall.
Pro Tip: Metasploit can be used to automate most of the processes coordinated after the exploitation phase, such as privilege escalation.
3. Wireshark: The Cyber Investigator
If data packets could speak, then Wireshark would be its voice. This packet analyzer captures and dissects live network traffic and is used by ethical hackers to monitor data flow in the network. Initially known as Ethereal, Wireshark has now become the biggest information and network analysis tool.
Wireshark since it provides mechanisms to decode packets into readable information is best suited for security analysis, troubleshooting, and reconstructing the network.
Why Wireshark Stands Out:
- Packet Capture and Inspection:
Capture packets traveling across wired or wireless networks and analyze their contents in detail. - Comprehensive Protocol Support:
With support for hundreds of protocols, Wireshark is versatile enough for virtually any network environment. - Data Filtering:
Create custom filters using syntax like ip.addr == 192.168.1.1 to isolate relevant traffic. - Export and Replay Traffic:
Save packet captures for offline analysis or replay them to understand network behavior. - Color Coding:
Highlight traffic patterns with color-coded rules to quickly identify anomalies or specific protocols. - Integration with Tools:
Combine Wireshark with other tools like Tshark (command-line packet analyzer) or network simulation software for deeper insights.
Getting Started with WireShark
1. Installation:
Download Wireshark from its official website. It’s free and supports all major platforms.
2. Capturing Packets:
- Launch Wireshark and select the network interface to capture traffic.
- Click the Start button to begin capturing packets in real-time.
3. Analyzing Packets:
- Use the packet list pane to view all captured packets.
- Click on a packet to see its details in the packet details pane.
4. Applying Filters:
Narrow your focus using display filters like:
- http to view HTTP traffic.
- ip.src == 192.168.1.1 to isolate packets from a specific IP source.
- tcp.port == 80 to filter TCP traffic on port 80.
5. Saving Captures:
Export captured traffic for future analysis or sharing with other analysts.
Examples of Wireshark Filters
1. Find All Traffic from a Specific IP:
ip.addr == 192.168.1.1
2. Filter HTTP Requests:
http.request
3. Identify DNS Traffic:
dns
4. Monitor FTP Activity:
ftp
5. Detect Suspicious Port Scans:
tcp.flags.syn == 1 && tcp.flags.ack == 0
Limitations of Wireshark
- Cannot Prevent Attacks:
Wireshark is a passive tool, meaning it observes traffic but cannot stop malicious actions. - Encrypted Traffic:
Wireshark struggles with analyzing encrypted data unless decryption keys are provided. - Resource-Intensive:
Capturing large volumes of traffic can be demanding on system resources.
Pro Tip: Use Wireshark together with enumeration tools in ethical hacking to capture network activity and analyze it effectively.
4. Burp Suite: The Web Guardian
Burp Suite is a tool to interactively penetrate web applications to find problems and take advantage of them. With its help, traffic interception and request modification become achievable as well as automated scanning, which makes it indispensable for ethical hackers and analyzers of the application layer.
Features That Shine:
- Intercepting Proxy:
Acts as a middleman between the browser and the server, allowing users to inspect and modify HTTP/S requests and responses in real-time. - Scanner:
Automatically identifies common vulnerabilities like SQL injection, XSS, and CSRF in web applications. - Intruder:
Performs automated attacks to test for security issues, such as brute force attacks and fuzzing inputs. - Repeater:
Lets you manually modify and resend requests to analyze application responses. - Sequencer:
Analyzes randomness in session tokens to detect weak or predictable session mechanisms. - Decoder:
Encodes and decodes data in various formats, such as Base64, URL, and HTML encoding. - Comparer:
Helps compare requests and responses to identify differences, useful for parameter tampering analysis. - Extensions (Burp App Store):
Extend Burp Suite’s capabilities using custom plugins and extensions, developed by the community or PortSwigger.
How to Use Burp Suite: A Quick Start Guide
- Setup:
- Download Burp Suite from the official website and install it.
- Configure your browser to use Burp Suite as a proxy.
- Intercept Traffic:
- Open the Proxy tab and enable interception.
- Navigate to a target application in your browser to capture requests and responses.
- Analyze and Modify Requests:
- Send intercepted requests to the Repeater or Intruder for further analysis or attacks.
- Scan for Vulnerabilities:
- Use the Scanner in the Professional edition to run automated vulnerability scans.
- Fuzz Inputs:
- Use the Intruder to test application inputs by sending multiple payloads and analyzing responses.
- Generate Reports:
- After testing, compile findings into detailed reports for developers or stakeholders.
Limitations of Burp Suite
- Community Edition Restrictions: It lacks most of the automation and the scanning capabilities which means it cannot be used for thorough testing.
- Steep Learning Curve: New users may take some time to manage it due to its compound functionalities.
- Cost: The Professional & Enterprise editions are paid applications, which can be expensive for small businesses or individuals.
5. John the Ripper: The Password Slayer
Passwords remain the initial line of defense between the unknown world and our personal lives, and a bad password is as good as a disaster. For the ethical hacker, John the Ripper is what it takes to challenge and improve password authentication.
John the Ripper is a password recovery and cracking tool created by Openwall. It functions in a way that either conducts a brute force or dictionary attack on hashed passwords to identify easily compromised passwords. Initially designed for Unix, they now have support for modern operating systems, such as Windows, Mac OS, and various distributions of Linux.
John the Ripper is primarily used for:
- Examining password strength in penetration testing.
- Reset forgotten passwords.
- Detecting insecure passwords in security reviews.
Highlights:
- Multi-Platform Support: Supports multiple operating systems such as Windows, Linux operating system, and the MAC operating systems.
- Wide Algorithm Compatibility: Supports a broad range of password hash types, such as:
- MD5
- SHA-1, SHA-256, SHA-512
- DES, Blowfish
- LM/NTLM (Windows hashes)
- bcrypt and many more.
- Customizable Cracking Modes: Offers multiple modes to suit different cracking scenarios:
- Single Crack Mode: Uses a similar username and password to achieve quick returns.
- Dictionary Mode: Entails a list of readily available passwords to be matched against a list of passwords.
- Incremental Mode: Tries all the permutations and combinations to make sure that nothing has been missed.
- Extensibility with Plugins: Develop new custom modules or rules to add more functionality to John in relation to specific environments.
- High Performance: Fast-oriented, has support for multithreading along with distributed password cracking.
- Compatibility with External Tools: Integrates well with various tools such as Hashcat and Hydra as additional features of the tool.
Why It’s a Must-Have:
John the Ripper is very crucial when it comes to analyzing the authenticity of a system. If passwords are the keys to a network, then John makes those keys almost uncrackable by any person.
How John the Ripper Works
- Hash Extraction:
Obtain the hashed passwords from a system’s password database. For Unix-based systems, this is often /etc/shadow or /etc/passwd. - Password Cracking Mode:
Select a cracking mode:- Use Single Crack Mode for fast tests.
- Load a dictionary file for Dictionary Mode to match common passwords.
- Run Incremental Mode for a comprehensive brute-force attack.
- Rule Application:
Apply rules to modify words in the dictionary, such as adding numbers, reversing words, or changing cases. - Cracking Process:
John tests password guesses against the hash using its built-in algorithms or additional plugins. - Output Results:
Successful matches reveal the cracked password, which can then be analyzed for strength improvement.
Example Use Case: Basic Commands
1. Install John the Ripper:
Download and install from the official website or use package managers like apt (Linux).
sudo apt install john
2. Run John with a Password Hash File:
john <hashfile>
3. Use Dictionary Mode:
Specify a wordlist to match passwords:
john –wordlist=<wordlist> <hashfile>
4. View Cracking Results:
john –show <hashfile>
5. Incremental Mode:
Run an exhaustive brute-force attack:
john –incremental <hashfile>
Pro Tip: Hydra can be used in conjunction with this tool in order to gain a more extensive password attack plan.
To download John the Ripper, Click Here.
6. Kali Linux: The Ethical Hacker’s Playground
Consider having all the tools of ethical hacking within your reach. That is Kali Linux, the operating system that is not just an OS but it is more like a cybersecurity environment.
Kali Linux is a strong operating system that is built on Ubuntu and it’s designed to support cyber security personnel as well as ethical hackers. Based on the Debian distribution it offers an effective toolkit for penetration tests, security audits, and forensic investigations. Kali Linux is Much More than a distribution, it has over 600 pre-installed tools, which makes the complicated work of assessing and strengthening the IT systems a breeze.
What’s Inside:
1. Pre-installed Security Tools
- Metasploit Framework: Exploit development and penetration testing.
- Wireshark: Network protocol analysis.
- John the Ripper: Password cracking.
- Nmap: Network scanning and vulnerability detection.
2. Live Boot Capability
Run Kali Linux directly from a USB or DVD without installation, ensuring portability and security.
3. Wide Platform Support
Compatible with a variety of devices, including PCs, virtual machines, Raspberry Pi, and Android devices.
4. Rolling Updates
A rolling release model ensures that Kali Linux stays up-to-date with the latest tools and features.
Getting Started with Kali Linux
- Download and Install
Visit Kali.org to download the latest ISO. Install it on a PC or virtual machine. - Explore Tools
Experiment with popular tools like Metasploit, Burp Suite, and Hydra. - Stay Updated
Use theapt-get updatecommand to keep tools and libraries current.
Why It’s a Game-Changer:
Kali Linux is great for novices and experts using penetration testing. It is the final ethical hacking platform ranging from certified ethical hacker tools download to advanced customizations.
Pro Tip: Use the live boot option to run Kali on any system without installation.
7. Nikto: The Web Server Watchdog
Nikto is a tool that will be guarding you when it comes to web server vulnerabilities. This tool quickly identifies vulnerable software, misconfigurations, and any other security flaws in a matter of minutes.
Key Features of Nikto
1. Thorough Vulnerability Checks: Nikto performs a deep scan for various security issues, including:
- Server misconfigurations
- Outdated software
- Cookie and Cross-sites scripting attacks
- SQL injection flaws
- Security Headers and Cookies report
2. ActiveX Plugin and Configuration Manager: Nikto has an extensible plugin architecture which lets users adjust the results by way of the types of Web servers and applications.
3. Advanced Reporting Options: Once the scan is done, Nikto creates complex reports in HTML, XML, or CSV that include all data needed to fix problems by security specialists.
4. Active and Passive Scanning Modes: Nikto comes with both the options, the active scan as well as the passive ones so that the testers can get the most out of security testing without necessarily going overboard.
Why Ethical Hackers Need Nikto:
- Scans for more than 6,700 recognized vulnerabilities.
- Determines which applications are no longer in use, and which servers are configured improperly.
- Compact and surprisingly powerful.
Ideal Scenario:
Utilize Nikto as one of the enumeration tools in ethical hacking to defend web servers before other hackers consider exploiting them.
Example Command to Use Nikto
To perform a basic scan of a web server, use the following command:
nikto -h http://example.com
This will start a scan on http://example.com and identify any vulnerabilities or misconfigurations on the server.
Pro Tip: When performing web application penetration tests, pair Nikto with Burp Suite to see even better results.
8. Hydra: The Login Cracker
If John the Ripper is the sword, Hydra is the battering ram. Ethical hackers often use Hydra to crack login credentials, giving it its primary purpose on the platform.
What Makes Hydra Powerful:
- Can support and handle multiple protocols such as SSH, HTTP, FT,P and many others.
- Designed for comfortable password cracking sessions and multithreaded.
- Free and very adaptable.
When to Use It:
Hydra stands out best when you are targeting to probe login weaknesses that different systems or applications have.
Pro Tip: Hydra should be used along with John the Ripper to confirm the password stability.
9. Aircrack-ng: The Wi-Fi Warrior
Since the advent of wireless networks, Aircrack-ng has been one of the essential tools for ethical hackers. It deals with attacking Wireless Fidelity (Wi-Fi) networks and breaking simple encryption.
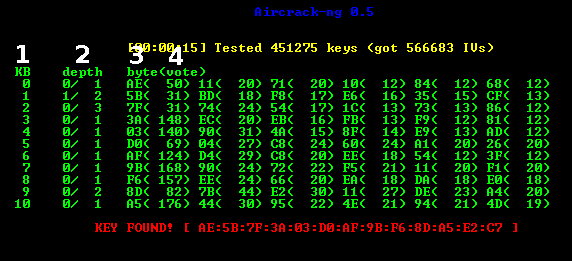
Key Features:
- Decrypt keys of the WEP, WPA, and WPA2-PSK security standards.
- Real-time traffic analyzing and packet capturing.
- It also possesses packet injection functionality for sophisticated testing.
Why It’s Essential:
Aircrack-ng aids ethical hackers in pinpointing vulnerabilities in wireless security configurations so that these are not prone to malicious attacks.
Pro Tip: For maximum effectiveness select a Wi-Fi adapter that complies with packet injection.
10. Maltego: The Data Whisperer
Knowledge is strength and Maltego assists you in making this knowledge work for you. The relationships between the data pieces are collected and shown by this OSINT tool which makes it useful in reconnaissance.
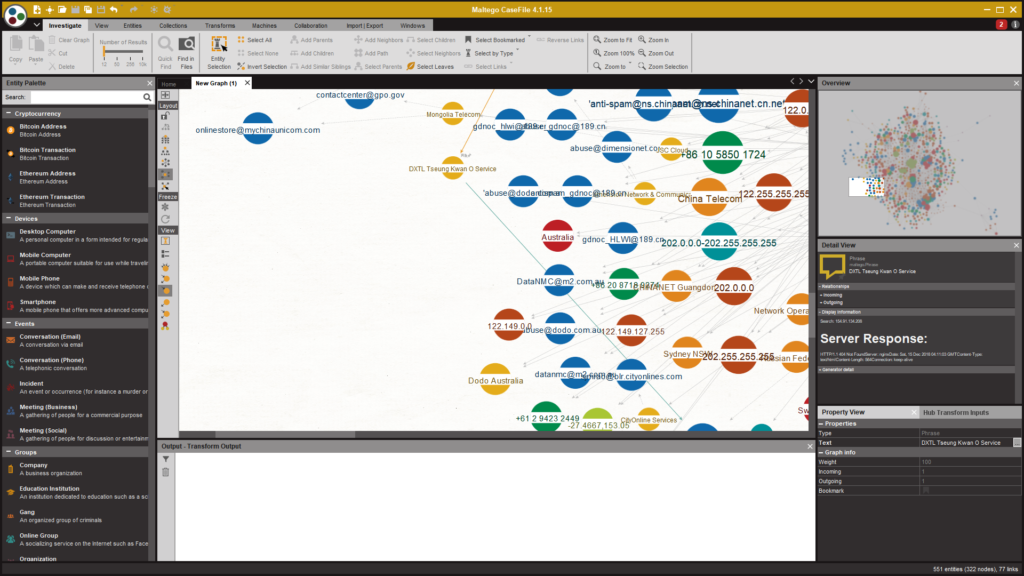
Standout Features:
- Can model relationships between people, organizations, and domains.
- Examines information found and collected in public sources.
- Very suitable for specific search approaches.
Real-World Application:
Maltego is most effective at the pre-attack stage because it reveals previously unsuspected connections that might be highly exploitable.
Pro Tip: Scanning tools should be used in combination with Maltego to get complete information on the target.
The Future of tools of ethical hacking
Ethical hacking is a constantly developing area of activity. Where the threats are advanced, so should the systems we employ in their defeat. From developing ethical hacking tools with Python to achieving the best levels of scanning; the name of the game is learning.
Final Thoughts:
- Delve deeper into each tool for ethical hacking to understand how it can be used to the best advantage.
- Take practice in some dummy systems before practicing with actual systems.
- It is always wise to seek permission before conducting any ethical hacking tests.